
Overview: SSL Certificates on a WLC?
• Internal HTTPS Server on the WLC enabled by default for Web
Administration & Web Policy (Web Authentication/Passthrough)
• Provides SSL encryption between Wireless Client & WLC to protect Web
Authentication credentials.
• Problem
End-Users receives a Security Warning when triggering the Web Policy page on
the WLC. A Self-Signed Certificate (SSC) is installed on the WLC by default.
• Solution
Deploy a 3” Party Certificate Signed by a Public CA
‘in this presentation we will outline the steps required to install a Chained 3t Party Certificate for Web Authentication/Passthrough (most common).
WLC Requirements
• Wireless Controller Code Version 5.1.151.0, or higher.
• OpenSSL 0.9.8 (1.0.0 is not compatible at this time).
• Up to Level 2 Certificates are supported on the WLC:
Level O: Device Certificate
Level 1: Device & Root Certificates
Level 2: Device, Intermediate, & Root Certificates
• 1024 and 2048-bit certificates are currently supported
Step 1 — Generate a CSR using OpenSSL 0.9.8
1) Install and open the OpenSSL application.
If using GnuWin32 OpenSSL for Windows: Open via Command Line:
C:\Program Files\GnuWin32\OpenSSL\bin\openssl.exe
2) Issue the following command:
OpenSSL>req –new -newkey rsa:1024 -nodes -keyout mykey.pem –out myreq.pem
Note: Either 1024 or 2048bНt requests can be used on the WLC.
3) Provide the requested information including Common Name.
Common Name must match DNS Hostname on the Virtual Interface
Note: don’t need A challenge password
4) Once complete, two files created:
myreq.pem — This is the request that will be sent to the CA
mykeypem — This is the key file which will be used once the certs arrive
Step 2 — Obtain the Certificates from your CA
1) Login to your Certificate Authority’s web portal (Microsoft CA), provide the
myreq.pem file when creating a new certificate, choose Web Server Template and click “Submit”.

2) Your CA will notify you when your Certificate is ready, and provide a
method for download (choose DER encoded, Download certificate chain).
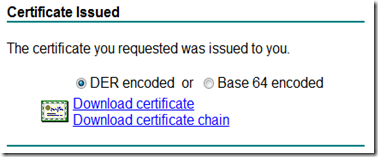
3) When downloading the certificate, ensure that you obtain the
following:
1) Device Certificate
2) Intermediate Certificate
3) Root Certificate
Step 3 — Chaining the Certificates
1) Once you have all the three certificates, copy and paste the contents
into a new file as follows:
----BEGIN CERTIFICATE ----
‘Device cert’
---- END CERTIFICATE ----
---- BEGIN CERTIFICATE ----
‘Intermediate CA cert’
---- END CERTIFICATE ----
---- BEGIN CERTIFICATE ----
‘Root CA cert’
---- END CERTIFICATE ----
2) Save the file as AII-certs.pem
3) Move the following files into the folder where OpenSSL.exe resides
(typically C:\Program Files\GnuWin32\OpenSSL\bin\):
• mykey.pem
• AII-certs.pem
Step 3 — Chaining the Certificates (Continued)
1) Open OpenSSL (via Command Line) and issue the following commands (in one line !!!):
a) openssl>pkcs12 –export -in All-certs.pem -inkey mykey.pem –out All–certs.p12
-clcerts -passin pass:check123 -passout pass:check123
b) openssl>pkcs12 –in All-certs.p12 –out final-cert.pem -passin pass:check123 –passout
pass:check123
Note: In this command, you must enter a password for the parameters –passin and
-passout. The password that is configured for the -passout parameter must match
the certpassword parameter that is configured on the WLC. In this example, the
password that is configured for both the -passin and -passout parameters is
check123.
If all is successful, you will now have a file called ‘flnal-cert.pem”. Move this
file into your TFTP Root Directory.
Step 4 — Downloading final-cert.pem to the WLC
1) Open your TFTP Server, and verify that final-cert.pem is within the Root
Directory on the server (OpenTFTPServer).
2) Login to you WLC via the Web GUI, and choose the following path:
Web GUI - Security - Web Auth - Certificate:
Check the box: "Download SSL Certificate"

3) When ready, click "Apply" in the upper right hand corner of the page.
4) Next, if installation successful click “Save Configuration” in the upper right hand corner of the page and then Reload WLC – “Save and Reboot” after click “Click Here” line. Wait 5-10 minutes till configuration saved and WLC booting up.
5) Go to MANAGEMENT – HTTP-HTTPS section and do the same as from Step 4 for management interface name.
Troubleshooting Tips:
1) OpenSSL does not Generate All-certs.p12 or final-cert.pem:
• Verify that the AII-certs.pem file has the certificates in the following order: device (top),intermediate, root.
• Verify that the mykey.pem file is the same used to originally create the CSR (myreq.pem).
• If an optional password was set within the CSR, ensure that this password was provided to the Certificate Authority when requesting the certificate.
2) Certificate fails to install to the WLC:
• Run the following debug:
debug transfer all enable
. Verify that the passin/passout password Ўs used when downloading to the WLC
3) Client still receives Security Warning after successful installation:
• Browse to the Web Policy page, and double-click the SSL icon in your browser to view the certificate. Review the certificate path.
Frequently Asked Questions:
1) Can I install the same certificate on multiple WLCs ?
Yes. The Virtual Interface IP address and hostname must be the same on au WLCs.
2) If I’m using a Guest Anchor WLC, where do I need to install the certificate ?
The 3rd Party SSL Certificate is only required on the Anchor WLC.
3) My company has a wildcard SSL certificate. Can I use this with the WLC ?
Yes, however please ensure that the certificate is a Level 2 or lower.
4) My certificates are not in .pem format. Can I convert these ?
Yes. You can use OpenSSL to perform the conversion:
or use the following Web-based tool:
==================================================================
Sources:
https://supportforums.cisco.com/thread/2015441
https://supportforums.cisco.com/videos/1871
https://supportforums.cisco.com/videos/1878
http://www.cisco.com/en/US/tech/tk722/tk809/technologies_configuration_example09186a00806e367a.shtml
Installing Third Party SSL Certificates for Guest Access
Installing a 3rd Party SSL Certificate for Guest Access part 2 of 2



